The ever-growing popularity of VoIP and use of Session Border Controllers (SBCs) means that security and protection for such technologies are increasingly important. Here’s a look at why the link between VoIP and SBC security is a vital consideration.
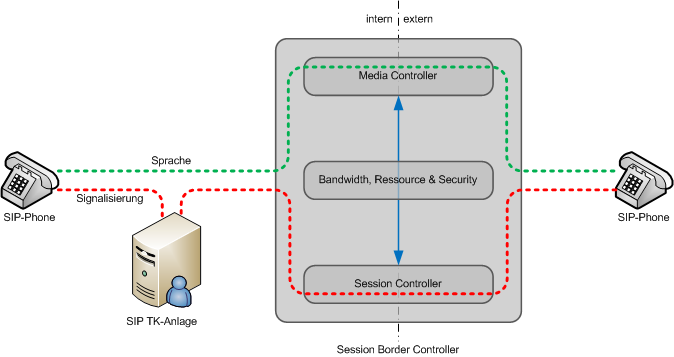
Image Credit
The potential pitfalls for security
Rather than being separate appliances, some SBCs are utilised within containers or virtual machines in the cloud, or alternatively on the premises of a company. They’re often deployed for protecting SIP-based VoIP networks, but their means of usage gives them a higher level of vulnerability and exposure to attacks.
In particular, DoS, or denial-of-service, is a prominent area of protection that’s required. As a result of SBCs being on the outer reaches of a network, it’s more susceptible to DoS threats, whether these are typical TCP SYN flooding, pings of death, or SBC-specific attacks. In terms of the latter, regulation overload and singling of Session Initiation Protocol are commonly employed.
When virtual containers are used for SBC administration, attacks such as with VMware aimed at the container itself can damage the app. While the SBC is compromised, it can’t directly assist or prevent such threats.
Data on the cloud can be particularly vulnerable if ample security measures aren’t taken. Cyber attacks and threats to businesses, infrastructure and institutions all increased in the UK throughout 2017 http://www.eweek.com/security/security-experts-warn-of-new-cyber-threats-to-data-stored-in-cloud.
Bridging the gaps to improve protection
With any aforementioned threats, their evolving sophistication poses another challenge for services, and thus, security likewise needs to evolve.
Firstly, it’s important to understand the technology, such as with VoIP https://www.idtexpress.com/blog/2018/02/24/wholesale-voice-termination-explained/, to address potential areas of weakness and vulnerability. Wholesale voice termination providers prioritise security and, therefore, play a significant role in protecting the service and their clients.
It’s then recommended to ensure only authorised users access the SBC system, and there are a few features within VoIP and SBC technologies that can help here. For instance, URL filtering will manage access to only certain IP addresses, while SBC access control lists can grant access to specified users. SBC security will also often cover singling to ward off service theft and media validation to protect VoIP services.
It’s important that VoIP and SBC systems work in tandem to secure their deployment and networks in the face of evolving cyber threats.













